// FileOverlap.cpp : Defines the entry point for the console application.
//
#include "stdafx.h"
#include
int cbCount = 0;
BOOL printfDetail = FALSE;
int loop_count = 200;
int successCount = 0;
int failedCount = 0;
#define COMPUTE_TIME(fun) \
{ \
DWORD begin = GetTickCount();\
fun;\
DWORD end = GetTickCount();\
printf("\r\n %s: loopCount:%d - cbCount:%d - successCount:%d - timeUsed:%d", #fun, loop_count, cbCount, successCount, end - begin);\
}
void CALLBACK MyFileIOCompletionRoutine(DWORD dwErrorCode, DWORD dwNumberOfBytesTransfered, LPOVERLAPPED lpOverlapped)
{
if(printfDetail) {
printf("\r\ndwErrorCode:%d - dwNumber:%d - offset:%d", dwErrorCode, dwNumberOfBytesTransfered, lpOverlapped->Offset);
}
cbCount++;
if(dwNumberOfBytesTransfered > 0) {
successCount++;
}
}
void useReadFileEx(LPCTSTR file)
{
HANDLE hFile = CreateFile(file, GENERIC_READ,
FILE_SHARE_READ | FILE_SHARE_WRITE | FILE_SHARE_DELETE, NULL, OPEN_EXISTING, FILE_FLAG_SEQUENTIAL_SCAN | FILE_FLAG_OVERLAPPED, NULL);
if(hFile == INVALID_HANDLE_VALUE) {
printf("bad file");
return;
}
OVERLAPPED overlap = {0};
const DWORD dwStepSize = static_cast(1024 * 1024 * 1);
const DWORD dwReadSize = dwStepSize - 3072;
LPVOID buffer = ::VirtualAlloc( NULL, dwStepSize, MEM_COMMIT, PAGE_READWRITE);
for(int i = 0; i < loop_count; i++)
{
overlap.Offset = (i % 1024) * dwStepSize;
::ReadFileEx(hFile, buffer, dwReadSize, &overlap, MyFileIOCompletionRoutine);
}
if(printfDetail){
printf("\r\nready wait.....");
}
while(loop_count > cbCount){
SleepEx(0, TRUE);
}
::VirtualFree(buffer, 0, MEM_RELEASE);
::CloseHandle(hFile);
if(printfDetail){
printf("\r\nuseReadFileEx:cbCount:%d ", cbCount);
}
}
void useReadFile(LPCTSTR file)
{
HANDLE hFile = CreateFile(file, GENERIC_READ,
FILE_SHARE_READ | FILE_SHARE_WRITE | FILE_SHARE_DELETE, NULL, OPEN_EXISTING, FILE_FLAG_SEQUENTIAL_SCAN | FILE_FLAG_OVERLAPPED, NULL);
if(hFile == INVALID_HANDLE_VALUE) {
printf("bad file");
return;
}
DWORD len = 0;
OVERLAPPED overlap = {0};
const DWORD dwStepSize = static_cast(1024 * 1024 * 1);
const DWORD dwReadSize = dwStepSize - 3072;
LPVOID buffer = ::VirtualAlloc( NULL, dwStepSize, MEM_COMMIT, PAGE_READWRITE);
for(int i = 0; i < loop_count; i++) {
overlap.Offset = (i % 1024) * dwStepSize;
if(!::ReadFile(hFile, buffer, dwReadSize, &len, &overlap)) {
if(GetLastError() == ERROR_IO_PENDING) {
GetOverlappedResult(hFile, &overlap, &len, TRUE);
}
}
}
::VirtualFree(buffer, 0, MEM_RELEASE);
::CloseHandle(hFile);
}
void useMoreReadFileEx(TCHAR (*files)[MAX_PATH], int count)
{
#if 1
for(int i = 0; i < count; i++) {
useReadFileEx(files[i]);
}
#else
OVERLAPPED overlap = {0};
const DWORD dwStepSize = static_cast(1024 * 1024 * 1);
const DWORD dwReadSize = dwStepSize - 3072;
LPVOID buffer = ::VirtualAlloc( NULL, dwStepSize, MEM_COMMIT, PAGE_READWRITE);
for(int j = 0; j < count; j++) {
HANDLE hFile = CreateFile(files[j], GENERIC_READ,
FILE_SHARE_READ | FILE_SHARE_WRITE | FILE_SHARE_DELETE, NULL, OPEN_EXISTING, FILE_FLAG_SEQUENTIAL_SCAN | FILE_FLAG_OVERLAPPED, NULL);
if(hFile == INVALID_HANDLE_VALUE) {
printf("bad file");
return;
}
for(int i = 0; i < loop_count; i++)
{
overlap.Offset = (i % 1024) * dwStepSize;
::ReadFileEx(hFile, buffer, dwReadSize, &overlap, MyFileIOCompletionRoutine);
}
}
SleepEx(0, TRUE);
#endif
}
void useMoreReadFile(TCHAR (*files)[MAX_PATH], int count)
{
for(int i = 0; i < count; i++) {
useReadFile(files[i]);
}
}
int _tmain(int argc, _TCHAR* argv[])
{
TCHAR path[MAX_PATH] = _T("c:\\package.zip");
TCHAR files[10][MAX_PATH];
int fileCount = 1;
if(argc < 3) {
printf("\r\nexample1: 1024 c:\1.zip");
printf("\r\nexample1: 1024 c:\1.zip 1");
printf("\r\nexample1: 1024 c:\1.zip 1 2");
printf("\r\nexample2: 200 c:\cc|1.zip,2.zip");
printf("\r\nexample2: 200 c:\cc|1.zip,2.zip 1");
printf("\r\nexample2: 1024 c:\cc|1.zip,2.zip 1 2");
return 0;
}
loop_count = _ttoi(argv[1]);
_tcscpy(path, argv[2]);
if(argc >= 3) {
TCHAR *pmain = _tcstok(path, _T("|"));
if(pmain != NULL) {
TCHAR *pfile = _tcstok(NULL, _T(","));
int i = 0;
for(i = 0; i < 10 && pfile != NULL; i++) {
_stprintf(files[i], _T("%s\\%s"), pmain, pfile);
pfile = _tcstok(NULL, _T(","));
}
fileCount = i;
}
}
if(argc > 3) {
printfDetail = argc > 4;
if(fileCount > 1) {
COMPUTE_TIME(useMoreReadFileEx(files, fileCount));
}else{
COMPUTE_TIME(useReadFileEx(path));
}
}else if(argc == 3) {
if(fileCount > 1) {
COMPUTE_TIME(useMoreReadFile(files, fileCount));
}else{
COMPUTE_TIME(useReadFile(path));
}
}
getchar();
return 0;
}
分类目录归档:wpt性能优化
etw的信息提取
https://docs.microsoft.com/en-us/windows-hardware/test/wpt/xperf-actions
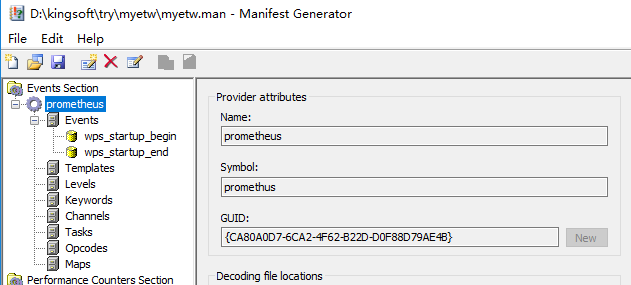
xperf -tle –i myetw.etl -o providers.csv -a dumper -provider {CA80A0D7-6CA2-4F62-B22D-D0F88D79AE4B}
https://docs.microsoft.com/en-us/windows-hardware/test/weg/instrumenting-your-code-with-etw
Copy your component to the location that was specified in your manifest by the resourceFileName attribute:
xcopy /y MyProviderBinary.exe %temp%
Register the providers:
wevtutil um etwmanifest.man
wetvutil im etwmanifest.man
Verify that the provider is visible:
logman query providers
Your provider name/GUID will appear in the list.
1.Start tracing:
xperf -start MySession -on MyEventProvider -f MySession.etl
# In that command line, -start gives the event collection session a name, and -on tells ETW that you want to collect events from your provider in this session. (There can be multiple -on arguments.)
2.Execute your workload.
3.Stop tracing:
xperf -stop MySession
@echo off
echo "clean session.."
xperf -stop app_session -d app_tmp.etl
xperf -stop -d base_tmp.etl
if exist app_tmp.etl (del app_tmp.etl)
if exist base_tmp.etl (del base_tmp.etl)
echo "open session.."
set now=%date:~0,4%%date:~5,2%%date:~8,2%_%time:~0,2%%time:~3,2%%time:~6,2%
set now=%now: =0%
echo %now%
xperf -start -on Base
xperf -start app_session -on CA80A0D7-6CA2-4F62-B22D-D0F88D79AE4B
echo "请启动prometheus应用。"
timeout 100
xperf -stop app_session -d app_tmp.etl
xperf -stop -d base_tmp.etl
xperf -merge base_tmp.etl app_tmp.etl prometheus_%now%.etl
xperf -tle -i abc_%now%.etl -o hardfaults_%now%.csv -a hardfault -file -bytes
xperf -tle -i abc_%now%.etl -o time_%now%.csv -a dumper -provider {CA80A0D7-6CA2-4F62-B22D-D0F88D79AE4B}
xperf -tle -i abc_%now%.etl -o pagefaults_%now%.csv -a dumper -provider {3D6FA8D3-FE05-11D0-9DDA-00C04FD7BA7C}
rem start wpa.exe abc_%now%.etl