https://docs.microsoft.com/en-us/windows-hardware/test/wpt/xperf-actions
xperf -tle –i myetw.etl -o providers.csv -a dumper -provider {CA80A0D7-6CA2-4F62-B22D-D0F88D79AE4B}
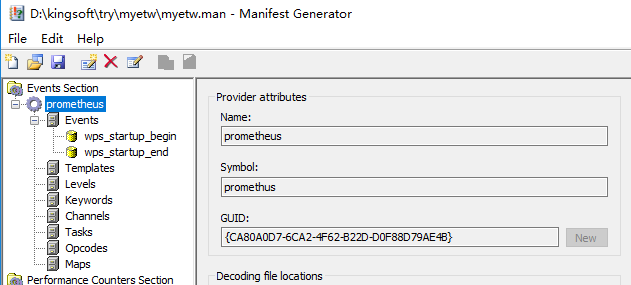
https://docs.microsoft.com/en-us/windows-hardware/test/weg/instrumenting-your-code-with-etw
Copy your component to the location that was specified in your manifest by the resourceFileName attribute:
xcopy /y MyProviderBinary.exe %temp%
Register the providers:
wevtutil um etwmanifest.man
wetvutil im etwmanifest.man
Verify that the provider is visible:
logman query providers
Your provider name/GUID will appear in the list.
1.Start tracing:
xperf -start MySession -on MyEventProvider -f MySession.etl
# In that command line, -start gives the event collection session a name, and -on tells ETW that you want to collect events from your provider in this session. (There can be multiple -on arguments.)
2.Execute your workload.
3.Stop tracing:
xperf -stop MySession
@echo off
echo "clean session.."
xperf -stop app_session -d app_tmp.etl
xperf -stop -d base_tmp.etl
if exist app_tmp.etl (del app_tmp.etl)
if exist base_tmp.etl (del base_tmp.etl)
echo "open session.."
set now=%date:~0,4%%date:~5,2%%date:~8,2%_%time:~0,2%%time:~3,2%%time:~6,2%
set now=%now: =0%
echo %now%
xperf -start -on Base
xperf -start app_session -on CA80A0D7-6CA2-4F62-B22D-D0F88D79AE4B
echo "请启动prometheus应用。"
timeout 100
xperf -stop app_session -d app_tmp.etl
xperf -stop -d base_tmp.etl
xperf -merge base_tmp.etl app_tmp.etl prometheus_%now%.etl
xperf -tle -i abc_%now%.etl -o hardfaults_%now%.csv -a hardfault -file -bytes
xperf -tle -i abc_%now%.etl -o time_%now%.csv -a dumper -provider {CA80A0D7-6CA2-4F62-B22D-D0F88D79AE4B}
xperf -tle -i abc_%now%.etl -o pagefaults_%now%.csv -a dumper -provider {3D6FA8D3-FE05-11D0-9DDA-00C04FD7BA7C}
rem start wpa.exe abc_%now%.etl